Lost your Office 2016 product key? How can I backup or transfer Office activation to another computer? If you need to reinstall Windows or Office but you’ve lost 25-character product key, here are all possible ways to find Office 2016 / 2019 product key, or backup your Office activation so you can restore it later.
Method 1: Find Office 2016 / 2019 Product Key from Microsoft Account
If you bought Office online (e.g. Microsoft Store) without physical disc, your product key is stored in your Microsoft online account or arrived in your email receipt. Just sign in to Services & subscriptions with your Microsoft account, locate the Office one-time purchase and then click on the “View product key” link.
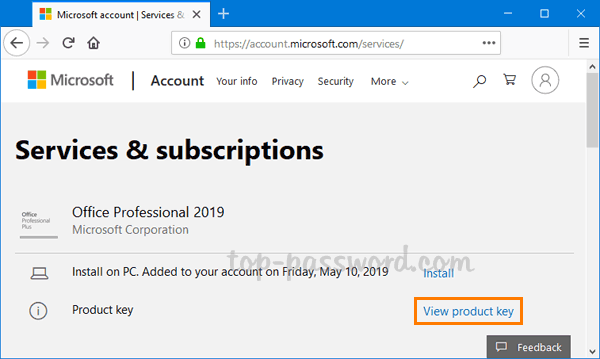
The Office product key associated with your Microsoft account will appear there. You can write down the product key and keep it somewhere safe.
Method 2: Find Office 2016 / 2019 Product Key from Windows Registry
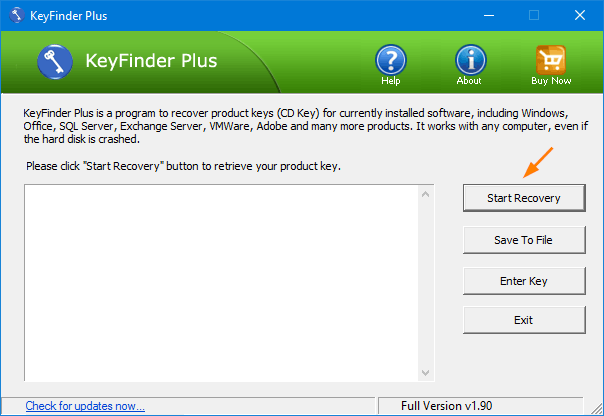
If Microsoft Office 2016 or 2019 came preinstalled on your computer or your product key sticker is totally unreadable, then try to decrypt and extract the product key from Windows registry using the third-party software like KeyFinder Plus.
After launching the KeyFinder Plus program, click on Start Recovery and then choose “From current system” from the drop-down menu. It will scan the registry for available activation keys for Windows, Office and other softwares installed on your computer.
Method 3: Backup and Restore Office 2016 / 2019 Activation
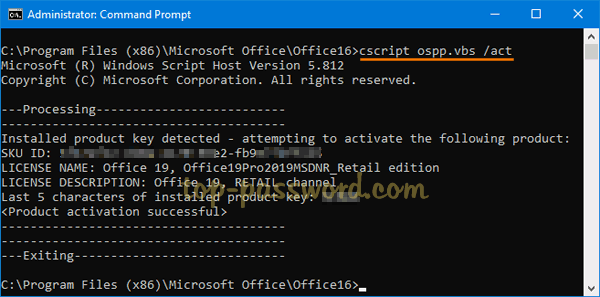
If you still couldn’t recover your Office product key, the last resort is to backup Office activation before reinstalling Windows or Office, so you can reactivate it later. To do this, open File Explorer and browse to the location: C:\Windows\System32\spp. Make a backup copy of all its folders / files and save them to an external USB drive for safe keeping.
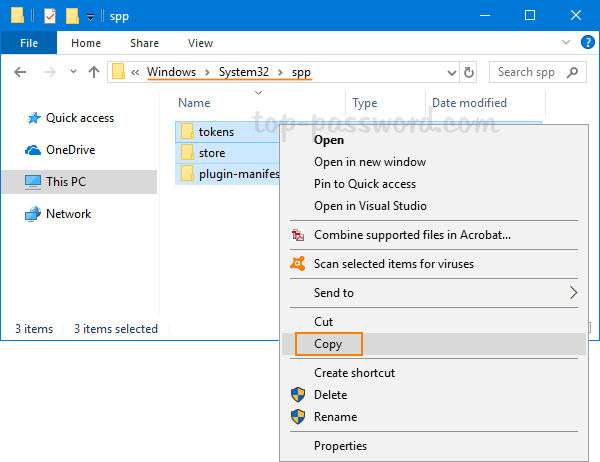
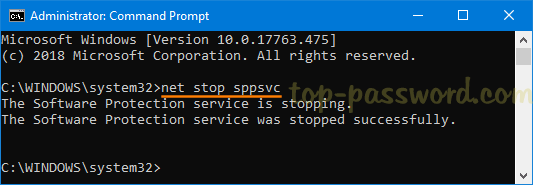
After installing a fresh copy of the same edition of Office, you can activate it by restoring the backup files to its original location: C:\Windows\System32\spp. When pasting the files, you may get an error messages informing me that “The action can’t be completed because the folder or a file in it is open in another program“. To get around this problem, just close the Office application and run the following command to stop the sppsvc service:
net stop sppsvc
When the files are restored, re-launch your Office application and you’ll find the product is already activated. You can also use this method to transfer Office activation over to another computer. But remember to deactivate Office on your old PC before restoring the activation to your new PC.