When you try to access a web page which contains a file hosted on a SMB server, Windows automatically sends your user name and NTLM credentials to authenticate. Although the credentials are not sent in clear-text, the attacker can crack them to recover your Windows password. To avoid leaking your account credentials, you can block NTLM (allowing only Kerberos) so Windows will no longer send your NTLM credentials to remote servers.
Method 1: Restrict Outgoing NTLM Traffic Using Group Policy
- Open the Local Group Policy Editor and navigate to:
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. On the right pane, double-click the “Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers” policy.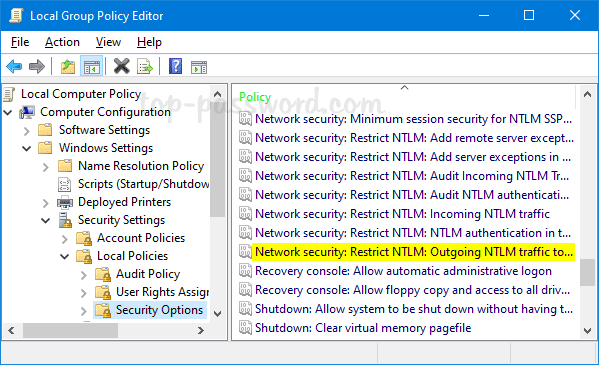
- Select Deny all from the drop-download list, click Apply and then OK.
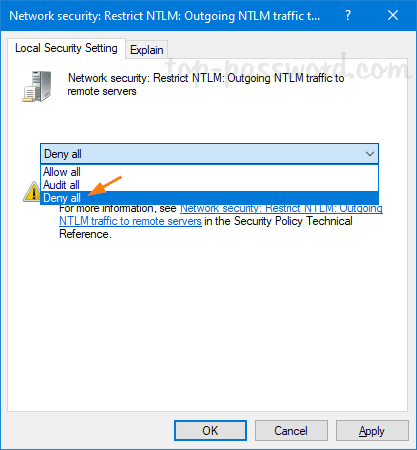
- Reboot your computer and Windows will no longer automatically send your NTLM credentials to a remote server when accessing a share.
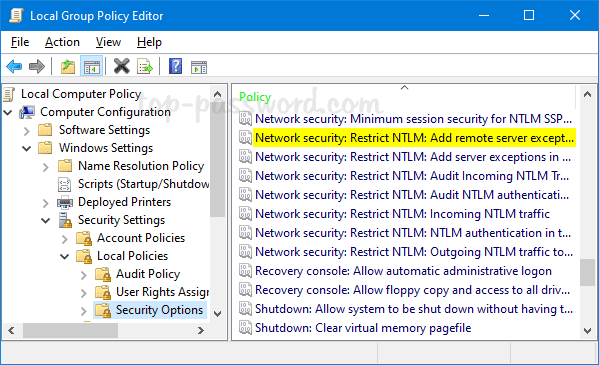
- If you need to add some remote servers to a whitelist, double-click on the “Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication” policy.
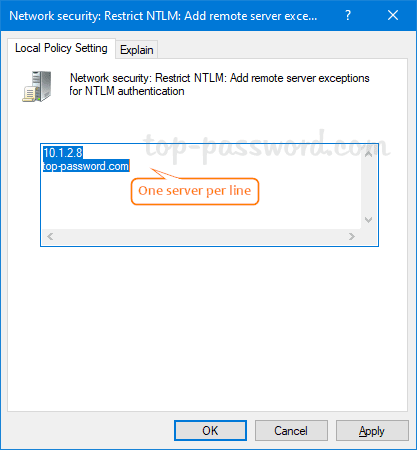
- Add the remote servers to the list of exceptions, click Apply and then OK.
Method 2: Restrict Outgoing NTLM Traffic Using Registry Tweak
- Open Registry Editor and browse to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0. Right-click on the MSV1_0 key, select New -> DWORD (32-bit) Value.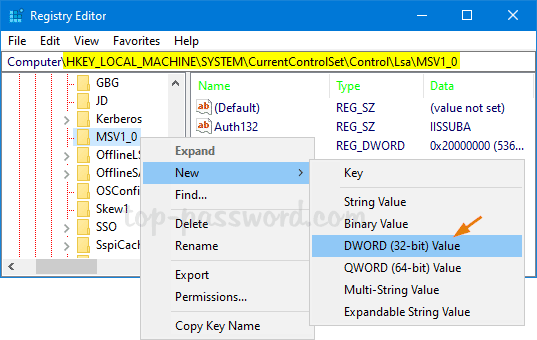
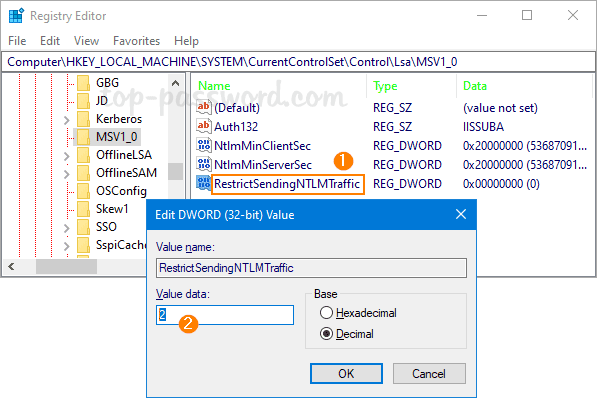
- Name the newly created DWORD RestrictSendingNTLMTraffic, then double-click it to set the value data to 2 and click OK.
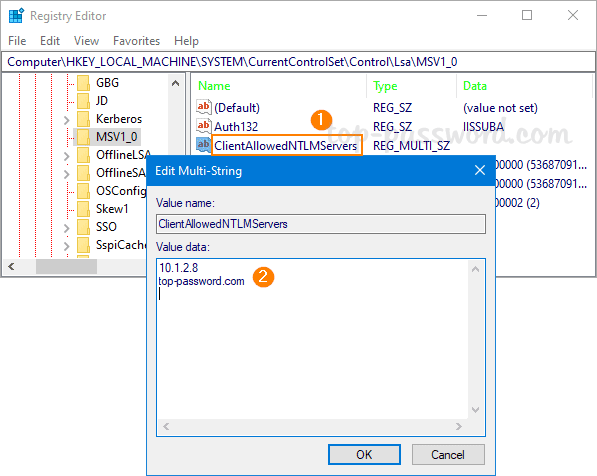
- If you want to add certain servers that you wish to whitelist, use the similar method to create a new DWORD named ClientAllowedNTLMServers. Double-click it and add remote servers which you allow sending NTLM credentials to.
- Reboot your computer to apply the changes. You can continue accessing files on remote servers which are whitelisted while stopping Windows from potentially sending your NTLM credentials over the network.